CS488 – Week 14 – Update
During the past week, I have submitted the second version of my paper. After submission, I have continued working on the final parts of the paper. These parts include finishing the social engineering results and making the recommended changes to certain images to enhance my paper. With the given feedback, I have also started making changes to my senior poster which is due Sunday.
CS 488 – Update – April 6th
This past week I mainly worked on the first draft of my poster. It was much easier to complete since I have the majority of my project finished. In the coming week, I plan to continue my testing with my virtual servers, Kali and Metasploitable. Luckily, I have not encountered any obstacles when trying to use these two for testing. I also plan to continue work on the second draft of my paper.
CS 488 – Week 7 – Elevator Pitch
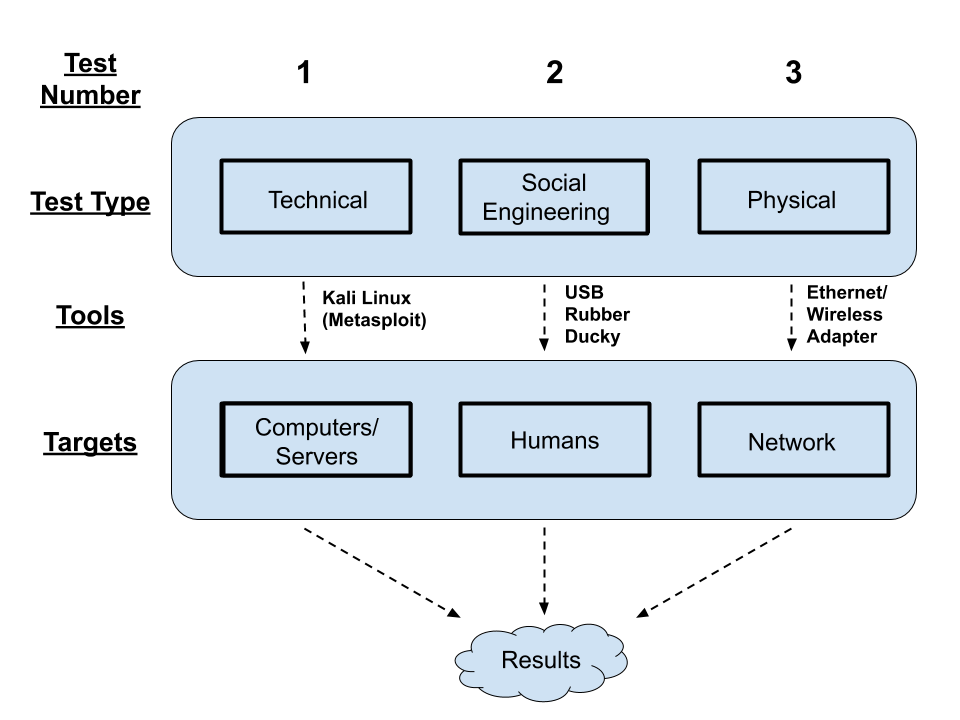
My project aims to develop a reproducible penetration test that can help secure a large network. Tests will come from three different avenues- physical and technical testing, as well as social engineering. The results from these tests will be put together in a final report and given to the appropriate people who can make appropriate changes as needed.
CS 488 – Week 5 – Update
This week I spoke with Charlie and gained clarity into how Earlham handles guest connections through ECOpen and from there does not allow access to the network within Earlham but simply gives access to the outside internet. I also started my Social Engineering test on Thursday. I ran into some speed bumps with that and am currently resolving. For this next week, I plan to talk to Aaron in ITS about NMAP and its use to possibly check for any ports that are left open and could be vulnerable. I plan to meet with him sometime early next week.
CS 488 – Week 4 – Update
This week, I continued my testing for the physical aspect of my project. During this testing, I tried to focus on ECOpen since it says there is no encryption associated with the network. Come to find out, there is still an authentication process that one must go through when trying to connect to ECOpen. So when I ran a packet sniffer on a device that was on an ECOpen channel, I could not see any data. (This is a good thing and was noted). I also finished preparing my social engineering test which will begin tomorrow, February 12th. This next week will consist of my social engineering test, processing results from physical test, and working on my paper.
CS 488 – Week 3 – Update
This past week I have really dug into my physical testing. Using Kali Linux and a wireless adapter (supports monitor mode), I was able to use commands to see which networks were available and from there, I could see all of the clients connected to each network. However, I only could see the BSSID (MAC Address) of each device, nothing more. I then went in to WireShark which showed me a little more data. I could potentially see what type of device it was. However, all data was encrypted in ECSecure. Trying to break the encryption was hard as we have hundred of users with different passwords. It’s not just a single password for the ECSecure network (that would be too easy to break). I plan to continue this testing and see what else I can find through ECOpen.
I have also started to set-up my Social Engineering experiment that way everything is ready when the start date arrives.
CS 488 – Week 2 – Update
This past week, I have started phase 1 of my project, testing the physical security of the network. Along with starting this phase, I started to write the Google survey that will be used w/ the social engineering experiment. I also ordered the hardware needed for the social engineering test. I have not encountered any obstacles. This next will I will continue to use WireShark to test the physical network using both a wireless and ethernet adapter.
CS 488 – Week 1 – Update
This week was mainly for refreshing myself on the details of my project. I finalized Charlie to be my advisor for 488 and set up a weekly meeting time with him. I also completed the 3 slide powerpoint in preparation for the presentation in the joint class of 388/488. I adjusted my timeline and plan to start the first phase of my project on Monday. I did not have any obstacles this week. Within this next week I plan to start the physical testing phase of my project.
CS388 – Week 12 -Update
During this week I met with Charlie to review feedback for the first draft of the proposal. I reconstructed this version for the 2nd draft. I also read some papers for the next pass. These were more directly related to the software I am going to use.
CS388 – Week 12 – Update
During the past week, I finished the first draft of my proposal and started to make those changes for the second draft. I have also continued reading some papers for their next pass. I continued to watch videos and read content related to the USB Rubber Ducky. I have started to put together some scripts that I would like to use for the attack. I also spoke with Charlie to refine my methods for the physical attacks I am going to implement. I now have a better/ more related CS implementation for this attack than what I previously had. During this next week, I am going to be working more with Metasploit on Kali Linux.
CS388 – Week 11 – Update
Much of my work this week has consisted on working through the first draft of the proposal as well as reading some papers for the next pass. I also found a couple other sources to use. These new sources were not research papers but rather articles related to my project.
CS388 – Week 10 – Update
During this past week, I have revised how I want to implement my social engineering attack. I want to use what is called a USB rubber ducky where you insert a MicroSD card into the USB. This card has payloads on it which you insert into the victims computer and then the payload is executed. Many different types of payloads can be written. These scripts are written in a language called duck script.
Charlie and I also discussed how to better implement my physical attack. This includes using a wireless adapter as well as ethernet cords to jack into ports around campus and see how easily I can get in.
CS388 – Week 9 – Updates
For this week, I wrote my proposal outline. During the next two weeks I will use this to construct the 1st draft of my proposal. I also spoke with Charlie about taking a different approach to the social engineering aspect of my project. Most of these I have found YouTube videos to demonstrate and describe the process but I have yet to find any hard research.
I also constructed more details for implementing the technical part of my project. This will also be discussed with Craig.
CS388 – Week 6 – Update
This week, I finalized who my advisor will be (Charlie). I also decided that I will be working on my security testing idea as my main project. To start this, I spoke with Brendan Post (IT) to discuss my ideas. He was happy to help me and I will be in further discussion with him as I move forward with my proposal.
I also found a couple other papers related to my idea. There was one that had much more lower level detail and actuially described the implementation of their testing. The researchers used Kali Linux to hack into a router through different ways such as SSH, Telnet, and SNMP. There were images that showed the commands they used. It was the first article I found to have a lot of low-level detail.
CS388 – Week 5 – Update
I spoke with Charlie this past week and we both decided that my first idea is my best one. So, I decided this was the one I was going to pursue my penetration testing idea and found 6 more articles for this.
A couple of the articles I found were about professors having/teaching a first-time hacking course. It was really cool to see the different designs of the classes. There was a general theme of keeping a subset of computers in a controlled environment and then allowing the students to work from there. One article included a complete description of their syllabus and the assignments of the course. This was helpful as it gave me an idea as to what software was being used in these courses.
CS388- Week4- Update
For this week, I created my annotated bibliographies for 2 papers of each of my 3 ideas. I also spoke with Charlie and refined 2 of 3 ideas. For my penetration testing idea, instead of making the project solely on the technical side, I want to basically have three phases of this project- technical, social, and physical. I plan to speak w/ Brendan Post in ITS and see how I could implement this at Earlham. I’d plan to publish the results of this testing to where other schools could do something similar.
In regards to the bibliography, one of my ideas is tracking Digital Footprints of users and I found a paper where the researchers created their own piece of software that was a blend of a password manager and an auditing service. I thought of being able to do something similar and create my own piece of software but with additional features.
CS388- Week3- Update
For this week, I updated my 3 proposal ideas and met with Charlie to review and seek his advice. Prior to this meeting, I found my 5 articles for each and used these discuss potential problems if each idea was used.
Post meeting w/ Charlie, I read a little deeper into the articles and now have a better idea on which proposal I may want to further investigate. Before I ead into the articles, I read the two PDF’s on Moodle about reading research papers and tried to implement this into my first and second pass of each article.
CS388 – Week 2 – Three Ideas
1st Idea
My 1st idea pretty much stayed the same as it was last week w/ some additional details. Instead of just testing/researching about network security, Charlie advised to look into physical security (open ports on servers, etc) and social security.
2nd Idea
Hacking into an air gapped device. Air gapped means that none of the devices interfaces have connectivity to the internet. Many believe this secures their device. I could look into and possibly use my own devices to test on.
3rd Idea
Today, everyone has some sort of digital footprint. I could envision writing software, that given parameters such as name, DOB, and age, could go on the web and find more information about that person.
Thanks to Charlie for helping guide me to finding these ideas.
CS388 – Week 1 – First Idea
- Name of Your Project
Penetration testing to show the weaknesses of businesses
- What research topic/question your project is going to address?
What results can be gained from businesses investing in someone do penetration
- What technology will be used in your project
Personal computer & Network Adapter
- What software and hardware will be needed for your project?
Kali Linux OS, Virtual Box
- How are you planning to implement?
Using the Network Adapter and Kali Linux’s built in features, access to a specific network becomes easier. Goals are described at the beginning and the attack is centered around those goals.
- How is your project different from others? What’s new in your project?
Other than Byron Roosa who graduated a few years ago, I am the only student who has had a security interest so this makes my project unique from others. My project is centered around helping the community. A penetration tests sole purpose is to help a business detect security flaws.
- What’s the difficulties of your project? What problems you might encounter during your project?
An obvious difficulty with my project is the legality associated with hacking. Getting a business to allow me to do this would take some convincing. Learning to navigate Kali Linux correctly would also be a difficulty.